In Brief
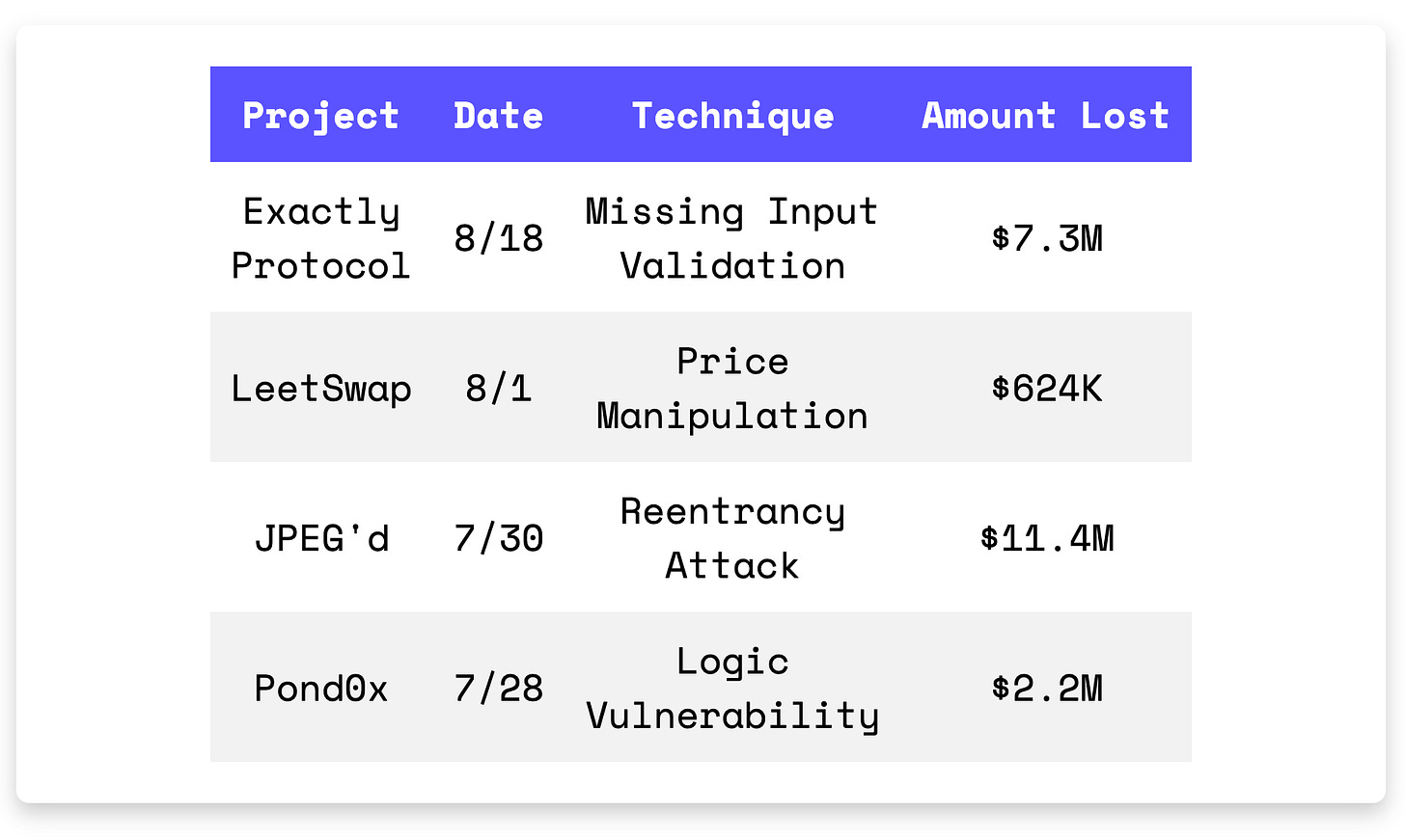
Exactly Protocol suffered a $7.3M loss due to missing input validation.
LeetSwap got exploited due to price manipulation.
JPEG’d lost $11.4M due to reentrancy vulnerability.
Pond0x coin launch was blamed for rug pull.
Hacks
Hacks Analysis
Exactly Protocol | Amount Lost: $7.3M
On August 18, the Exactly Protocol exploit on the Optimism Mainnet resulted in a $7.3M loss. The root cause was the public leverage() function in the DebtManager contract of Exactly Protocol. This function was missing proper input validation. The attacker exploited this vulnerability by passing in an invalid market address when using the leverage() function and created a UniswapV3 liquidity position with WETH and a fake token. Due to the lack of input validation, the attacker could manipulate the _msgSender parameter to target victim addresses and drain their funds.
Exploit Contract (on Optimism Mainnet): 0x16748cb753a68329ca2117a7647aa590317ebf41
Transaction Hash: 0x3d6367de5c191204b44b8a5cf975f257472087a9aadc59b5d744ffdef33a520e
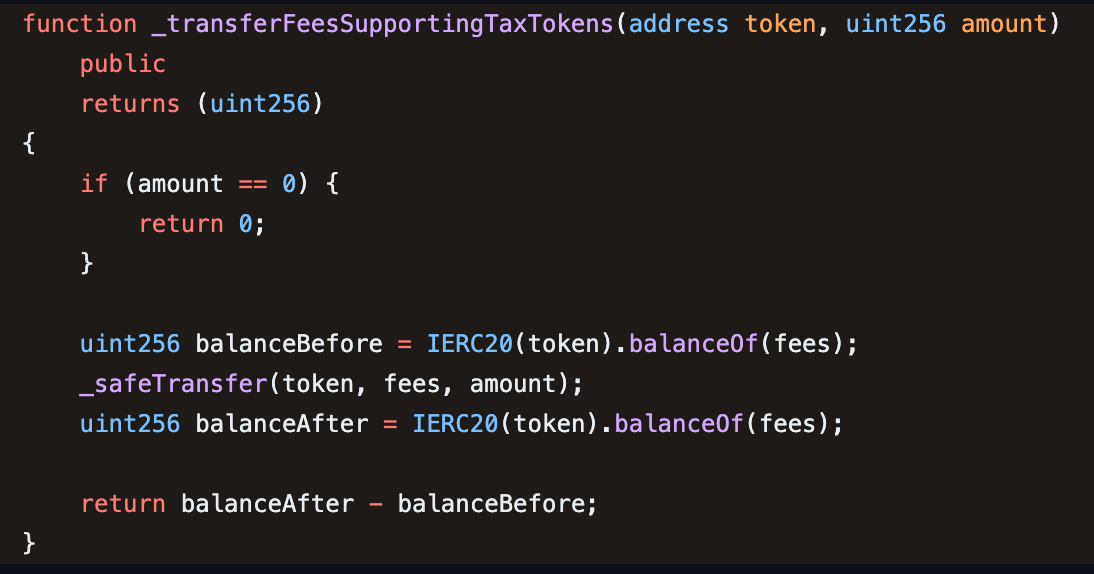
LeetSwap | Amount Lost: $624K
On August 1, the LeetSwap exploit on the Base Chain resulted in a $624K loss due to a price manipulation vulnerability. The root cause of the exploit was the incorrect visibility of the _transferFeesSupportingTaxTokens() function in the LeetSwapV2Pair contract. This function was meant to be private, but it mistakenly had a public visibility specifier. This mistake enabled the attacker to invoke this function to transfer tokens to LeetSwap's fee collection address. This reduced the liquidity of the axlUSD token, leading to an artificial price increase and allowing the attacker to make a profit from this manipulation.
Exploit Contract (on Base Chain): 0xEA8f89F47f3D4293897b4fe8cB69B5C233b9f560
Transaction Hash: 0xbb837d417b76dd237b4418e1695a50941a69259a1c4dee561ea57d982b9f10ec
JPEG’d | Amount Lost: $11.4M
On July 30, the JPEG’d exploit on the Ethereum Mainnet resulted in a $11.4M loss due to a reentrancy attack. The attacker exploited Curve Finance’s Factory Pool contract by invoking the remove_liquidity() function while reentering the add_liquidity() function. This led to an issue where the total_supply amount wasn't updated during the reentry into the add_liquidity() function. The attacker made a profit by manipulating the pETH token price. The lending platform reported recovering nearly $10M of assets and offering a 10% white hat fee to the exploiter.
Exploit Contract: 0x9848482da3ee3076165ce6497eda906e66bb85c5
Transaction Hash: 0xa84aa065ce61dbb1eb50ab6ae67fc31a9da50dd2c74eefd561661bfce2f1620c
Pond0x | Amount Lost: $2.2M
On July 28, the Pond0x exploit resulted in a $2.2M loss due to a contract logic vulnerability. The directTransfer() function in the vulnerable contract allowed users to transfer PNDX tokens from any address. During the launch of the token, traders purchased PNDX tokens, increasing the token price. The exploiter then revoked the directTransfer() function to transfer the minted PNDX tokens and sold them for profit. This led some investors to accuse the platform of a rug pull.
Exploit Contract: 0x1d4214081985ad20aa3ca93a2206ae792635cbec
Transaction Hash: 0x486a39badd5c0601c9e5d68066a035684edc97f35362567f66c7855f923a62a8