In Brief
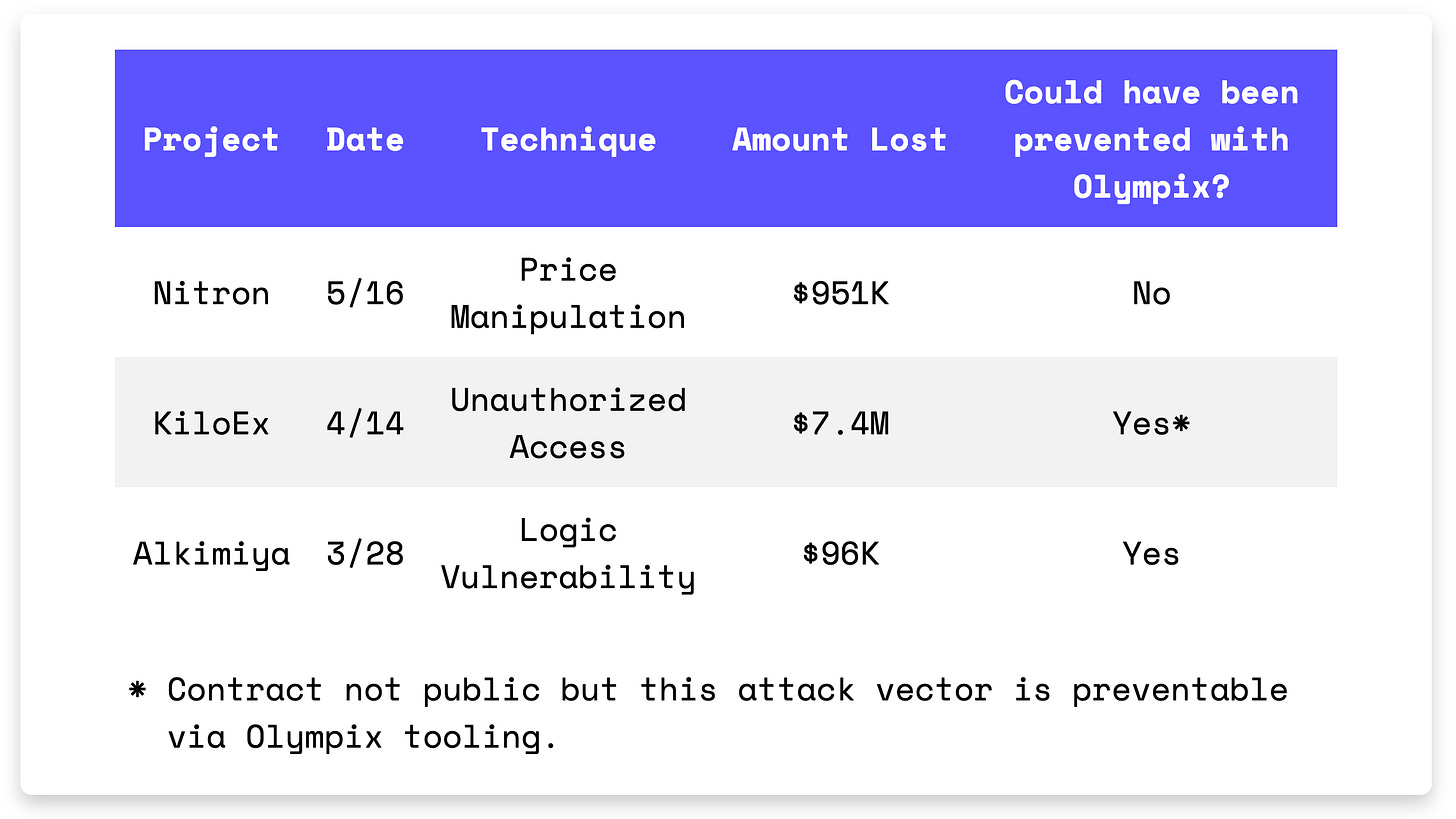
Nitron suffered a $951K price manipulation attack.
KiloEx was exploited for $7.4M after missing access controls.
Alkimiya lost $96K due to an unsafe integer conversion.
Hacks Analysis
Nitron | Amount Lost: $951K
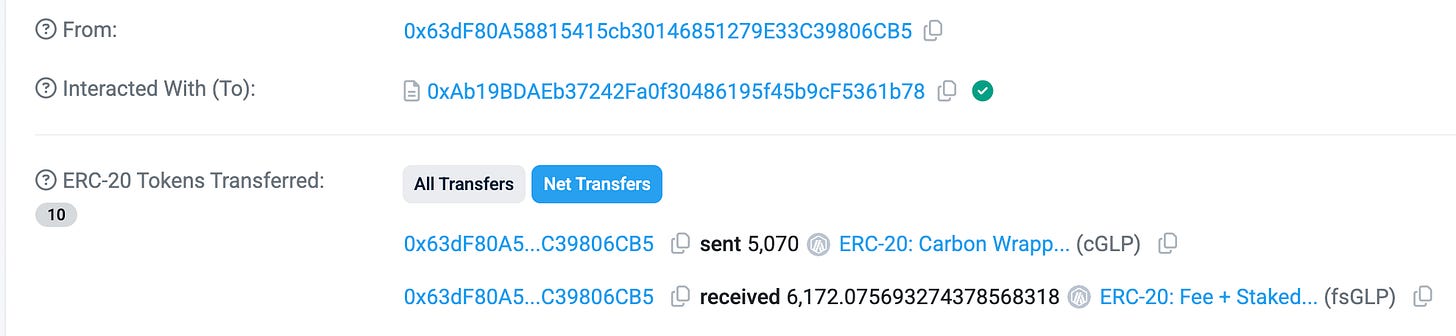
On May 16, the Nitron (on Demex) exploit on the Arbitrum chain resulted in a $951K loss due to a price manipulation attack. The attacker donated fsGLP tokens to a low-TVL dGLP vault, significantly increasing the supply and artificially inflating the token price. Nitron’s oracle used this inflated rate to calculate the value of dGLP. The attacker then used the overpriced dGLP as collateral to borrow other assets and make a profit. Nitron confirmed that they will introduce stricter withdrawal protections and on-chain TVL-based circuit breakers.
Exploited Contract (on Arbitrum): 0xab19bdaeb37242fa0f30486195f45b9cf5361b78
Transaction: 0x2bd26aee4b4f6de3a3b3806e334ea192deab682e00fa6707c5ecf2289392096d
KiloEx | Amount Lost: $7.4M
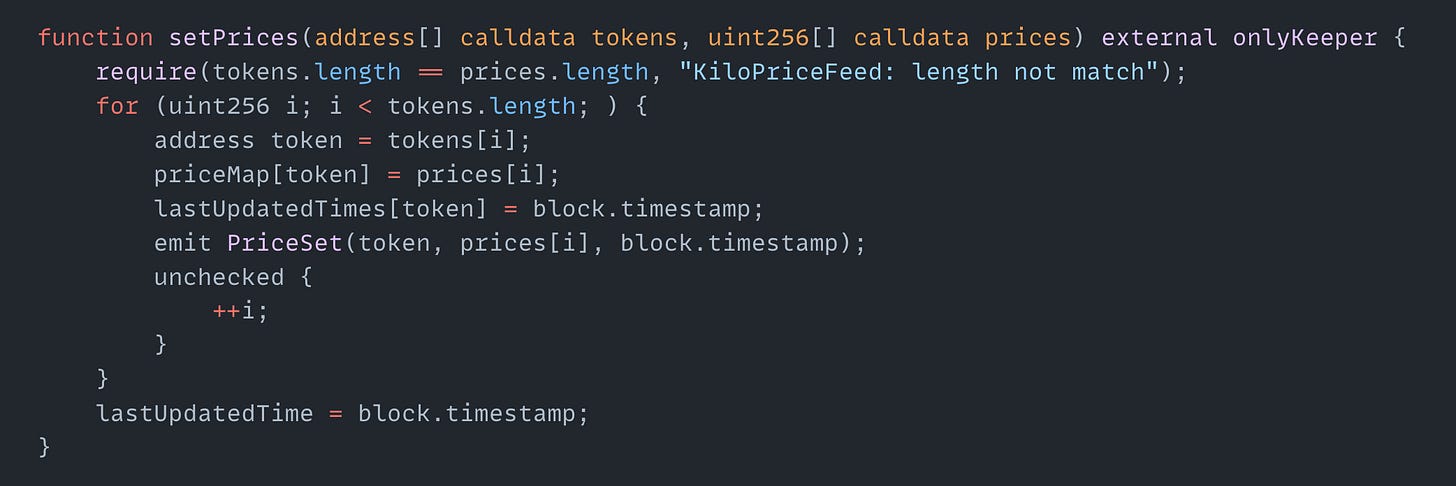
On April 14, the KiloEx exploit on the Base chain resulted in a $7.4M loss. The root cause of the exploit was missing access control in the setPrices() function in the KiloPriceFeed contract. The setPrices() function allowed unauthorized calls to increase or decrease the token price. By submitting a forged signature, the attacker manipulated ETH prices, initially setting it to $100, then opening a leveraged long position. Later the attacker set the price to $10,000, closed the long position and made a profit.
Exploited Contract (on Base): 0x22c40b883b5976f13c78ee45ead6b0cdc192dae5
Transaction: 0x6b378c84aa57097fb5845f285476e33d6832b8090d36d02fe0e1aed909228edd
Alkimiya | Amount Lost: $96K
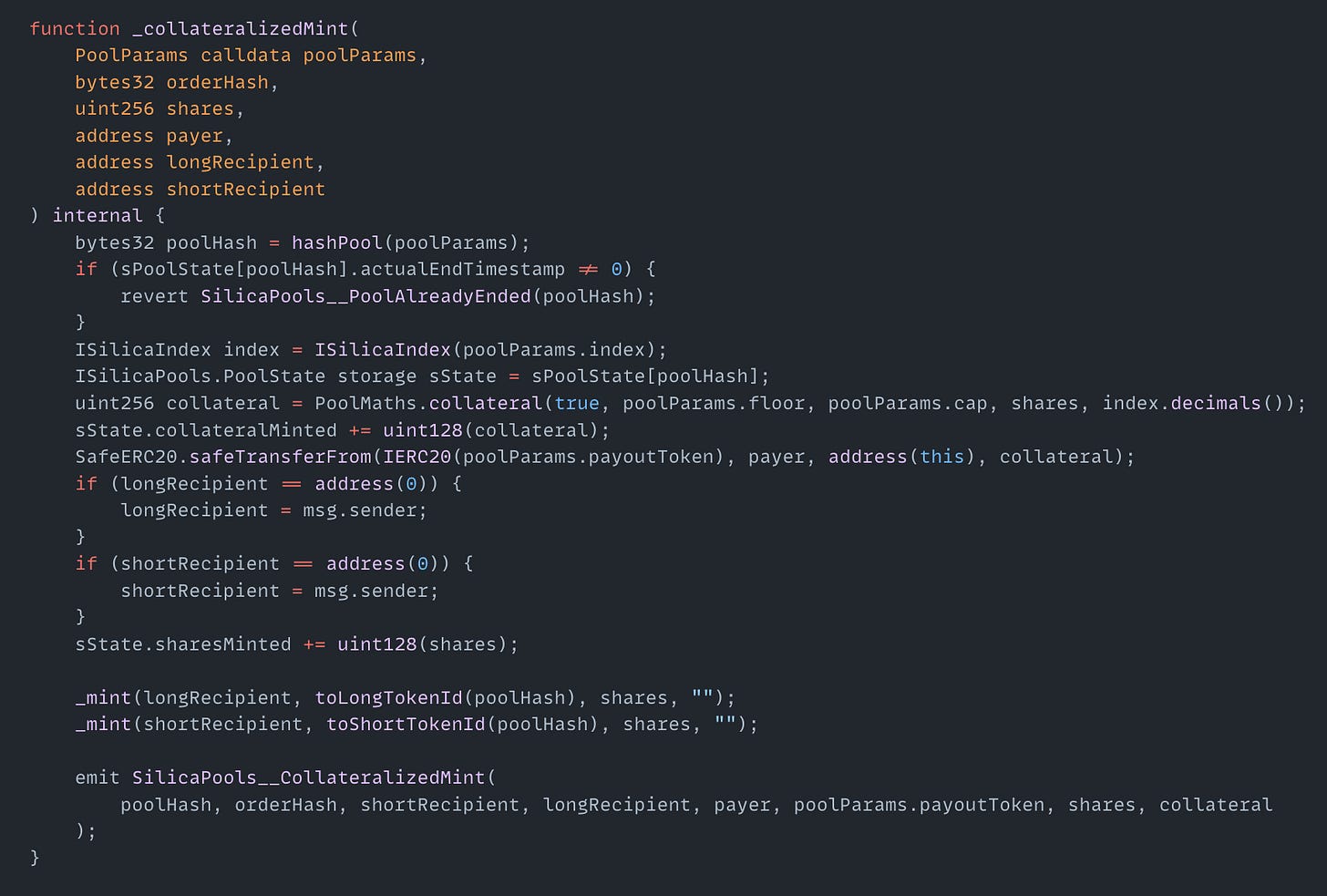
On March 28, the Alkimiya exploit on the Ethereum mainnet resulted in a $96K loss. The root cause of the exploit was that the private collateralizedMint() function did not validate the integer size when converting from uint256 to uint128. The attacker used a flash loan to call collateralizedMint() with a request for 2^128 + 1 shares. The function converted this value to a 128-bit integer without bounds checking and reduced the value to 1 share. The attacker then transferred out 2^128 - 1 shares, leaving 2 shares in the contract. When the attacker redeemed the balance, the contract miscalculated and returned more WBTC than expected.
Exploited Contract: 0xf3f84ce038442ae4c4dcb6a8ca8bacd7f28c9bde
Transaction: 0x9b9a6dd05526a8a4b40e5e1a74a25df6ecccae6ee7bf045911ad89a1dd3f0814