In Brief
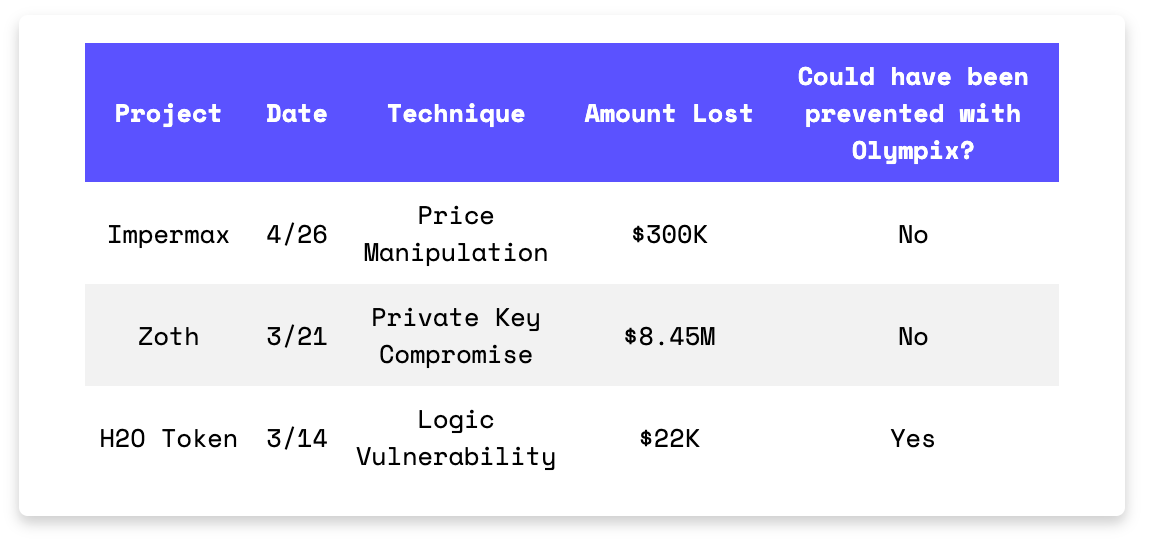
Impermax lost $300K to a price manipulation attack involving flash loans.
Zoth suffered an $8.45M exploit after the deployer wallet was compromised.
H2O Token lost $22K due to insecure on-chain randomness.
Hacks Analysis
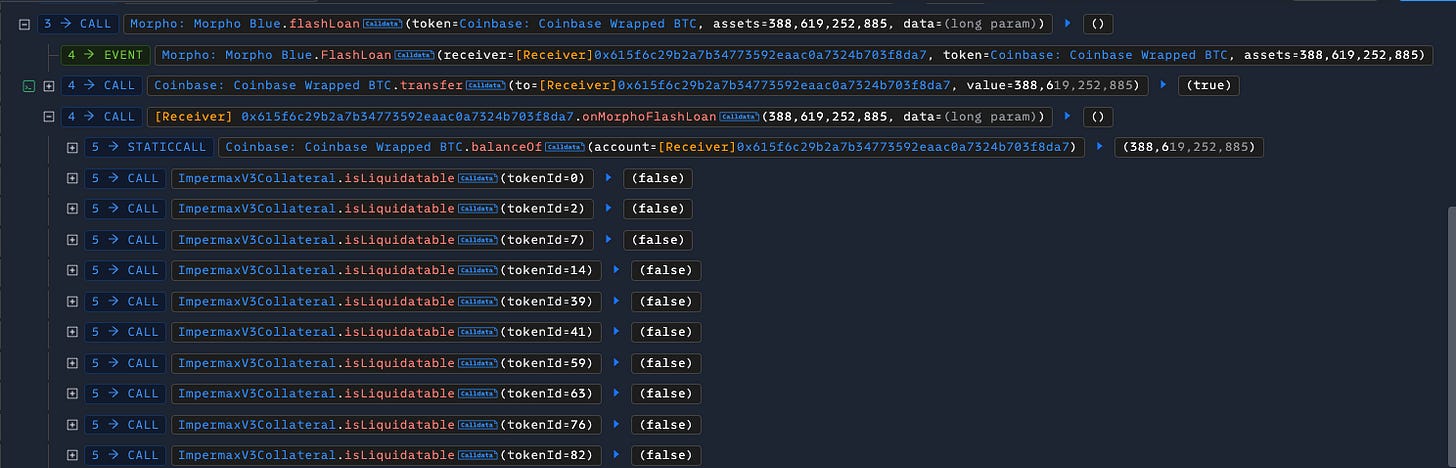
Impermax | Amount Lost: $300K
On April 30, the Impermax exploit on the Base network resulted in a $300K loss due to a price manipulation attack. The attacker used a flash loan to open a position on a low-liquidity Uniswap V3 pool, manipulated the price to accumulate uncollected fees, and borrowed against this inflated collateral. By compounding the fees at a manipulated price tick, the position's value was artificially reduced, allowing the attacker to make a profit.
Exploited Contract (on Base): 0xb362479915f2d24a284dd5e6742c4f619ad0453a
Transaction: 0xad4fc3156666d5402f00dcfd5c183493d283f4166a6dd581dd8c0a895e826a56
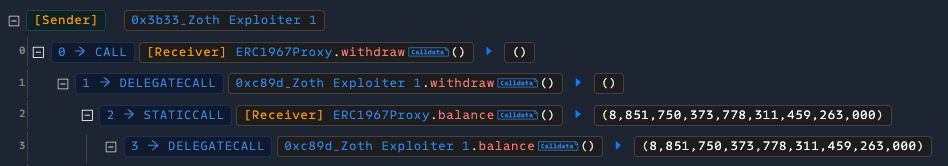
Zoth | Amount Lost: $8.45M
On March 21, the Zoth exploit on the Ethereum mainnet resulted in an $8.45M loss due to compromised access control. The attacker gained control of the deployer wallet, which held admin privileges over a critical proxy contract. Using this access, they upgraded the proxy to a malicious implementation that allowed unauthorized fund withdrawals. The Zoth team acknowledged the incident and offered a $500K bounty.
Transaction: 0x33bf669d125d11c432ac9b52b9d56161101c072fd8b0ac2aa390f5760fb50ca4
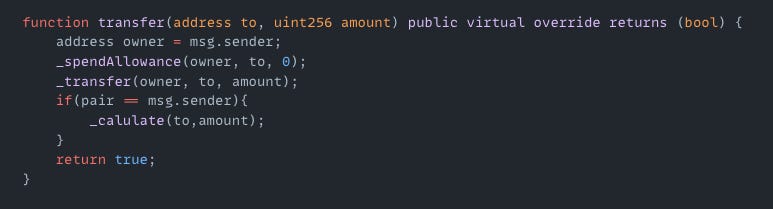
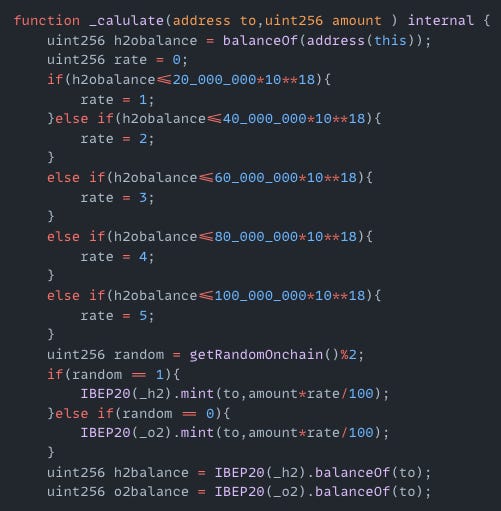
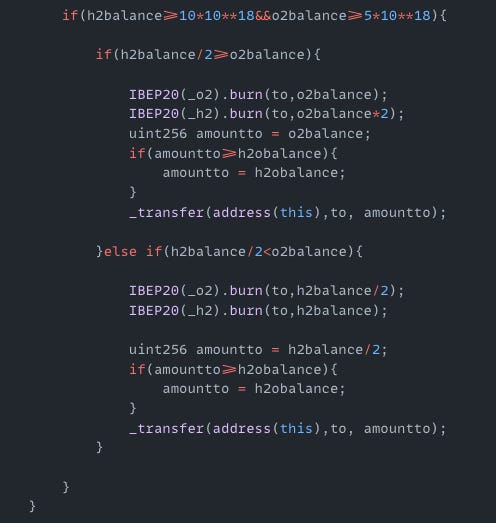
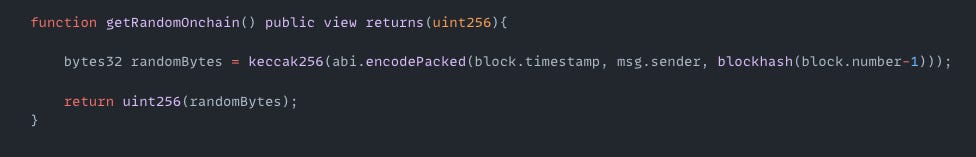
H2O Token | Amount Lost: $22K
On April 26, the H2O token exploit on the BSC resulted in a $22K loss. The root cause of the attack was insecure on-chain randomness that relied on predictable parameters. The attacker called the transfer() function and triggered the private _calulate() function which minted H2 and O2 tokens using insecure randomness derived from block.timestamp, block.number, and msg.sender. Since these values were predictable, the attacker was able to mint tokens and make a profit.
Exploited Contract (on BSC): 0xe9c4d4f095c7943a9ef5ec01afd1385d011855a1
Transaction: 0x729c502a7dfd5332a9bdbcacec97137899ecc82c17d0797b9686a7f9f6005cb7